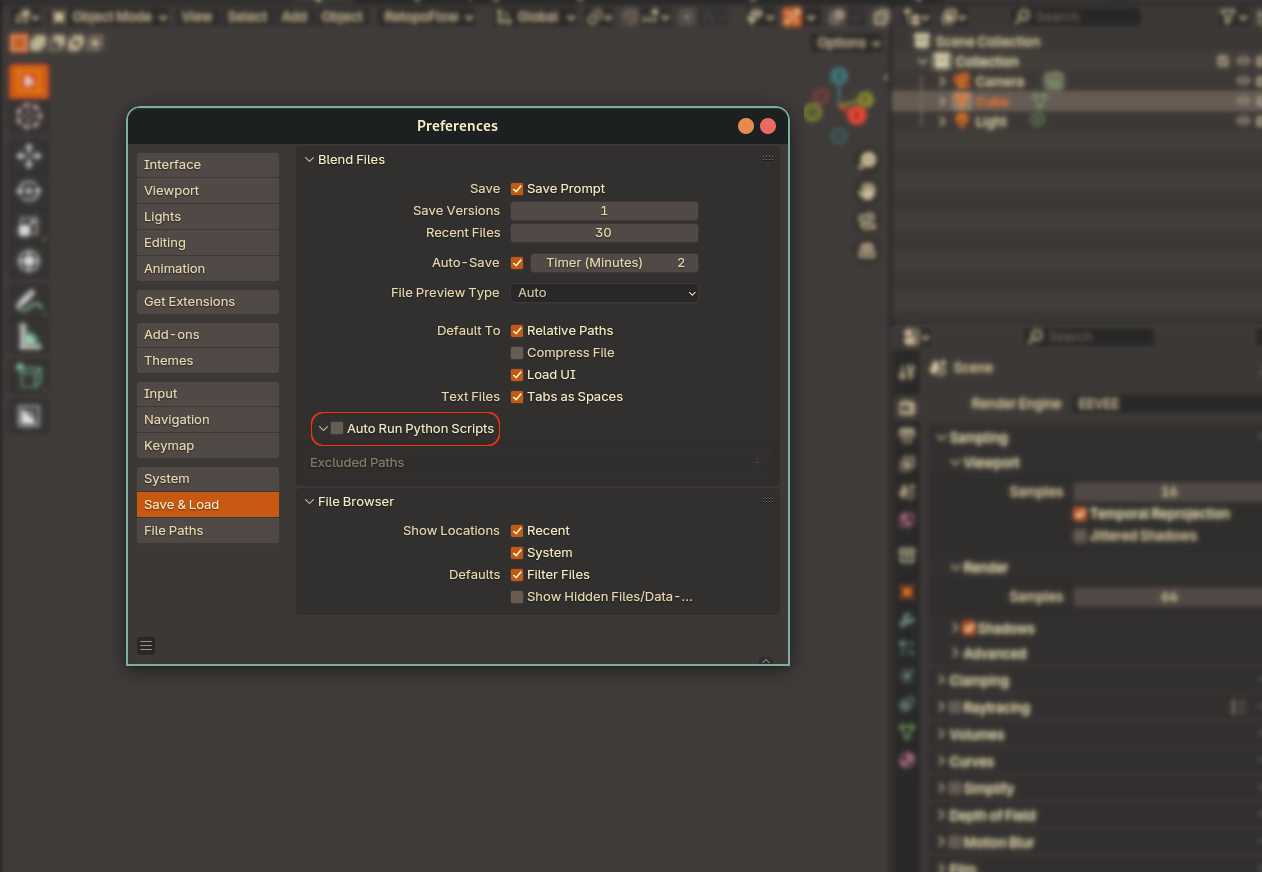
Blender includes a feature called Auto Run Python Scripts, found in Edit → Preferences → Save & Load. Its purpose is convenience: many Blender projects rely on Python scripts to automate rigging, generate user interfaces, or control rendering processes. When Auto Run is enabled, these scripts execute automatically whenever a .blend file is opened, saving artists from manually enabling scripts for every project.
By default, Blender will prompt the user when opening a file with an ‘untrusted’ script, but enabling Auto Run removes this prompt. So it’s good idea to leave if off by default. Naturally this is generally safe if you only open files from trusted sources, such as your own projects, assets you create or curated libraries. The real threat arises when opening .blend files from unknown or unverified sources, where a malicious Python script could execute automatically and attempt to install malware such as StealC V2 recently discovered and widely discussed.
It’s important to note that this isn’t a flaw in Blender itself. It’s a feature designed for workflow efficiency. The security risk comes from executing unverified scripts, not from the Auto Run setting being enabled per se. Keeping Auto Run enabled is fine for trusted assets, and you can combine it with general safe practices: verifying the source of files, sandbox-testing unfamiliar assets, and using formats that don’t rely on scripts, such as FBX or GLB, when possible. In our models either built in-house or curated carefully. Either when in doubt feel free to reach to us.